Services
Forensic Analysis
The forensic analysis of computer systems has the objective of finding what happened during a security incident. It seeks giving an answer to the questions that usually surround every incident:
- Which is the problem’s origin
- Which information actives were affected and to what extent
- When did the incident happen
- Where did it origin and towards which actives was it directed
- Etcetera
From esCERT-UPC we participate in both private forensic analysis and in those related to juridical processes, following at every moment a strict forensic methodology.
Our forensic analysis services are focused to those organizations that have suffered attacks, intrusions and/or information robbery, as to the wronged that require an investigation process where digital data is involved: emails, web pages, etcetera.
Using the most advanced techniques allow the esCERT’s security team to help to recover lost information over practically any kind of device and operative system.
Vulnerabilty management
The GUAITA platform, developed by us, has as main objective to keep System Administrators informed about the new
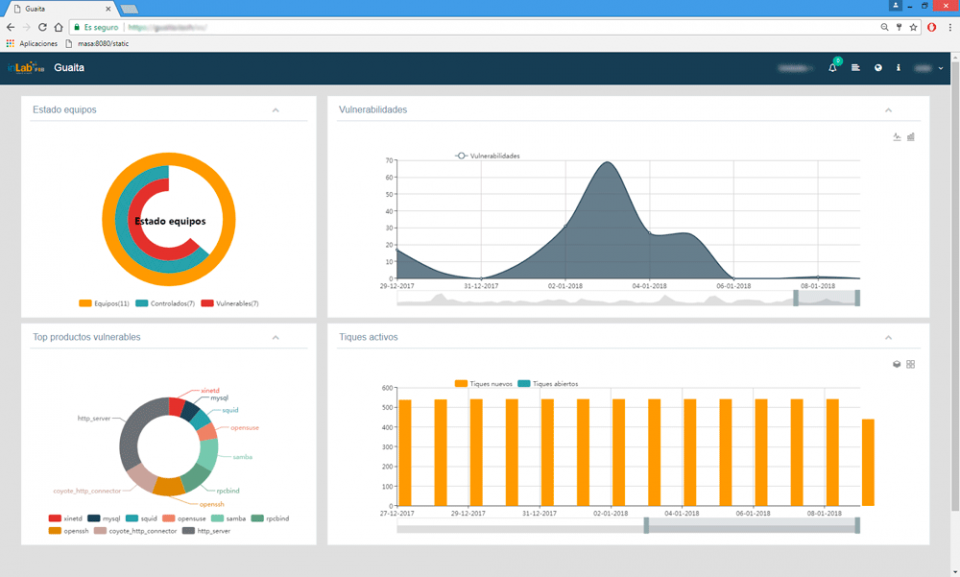
vulnerabilities that arise in operating systems, software, devices, etc. in order to help them prevent intrusions in their computer systems.
All the notices published in GUAITA allow to knowing thoroughly each vulnerability, the impact that its exploitation can have as well as the measures to take to update the affected systems.
GUAITA offers the System Administrators a personalized panel to their needs from where they can:
- Manage your servers and the services / products associated with them
- Review and validate the vulnerability alerts that affect them
- Generate reports and statistics on the evolution of alerts and vulnerabilities
Training
For over 15 years, our professionals have helped in the education on the security field to all kind of entities: CCN-CERT, Mossos d’Esquadra, Generalitat de Catalunya, etcetera.
Within the collaboration contract with Universitat Politècnica de Catalunya (UPC), from esCERT-UPC we periodically impart different courses of security addressed to all the university community.
In the same way, from the perspective of divulgating all the related computer security aspects, from esCERT-UPC we also offer personalized formation courses to companies and external technicians.
Some courses usually imparted are:
Audits
From esCERT-UPC we offer a personalized service of audits oriented to both web environments and systems and networks, with the aim of recommending mechanisms to improve the security of the organization’s information systems.
OWASP metodology:
Web application audits are necessary to avoid possible intrusions in the systems due to vulnerabilities of the software used in them.
The tests that applications go through, compatible with OWASP methodology, are enumerated right below:
Search of information, examination of the platform and the application
Revision of the platform configuration
Revision of the authentication processes
Revision of the sessions management (and possible identity thefts)
Revision of the authorization processes
Revision of the input validation errors
OSStMM metodology:
The OSStMM (Open Source Security Testing Methodology Manual) from the Institute for Security and Open Methodologies (ISECOM) is based on the analysis of each component and service of information systems in order to audit them and identify potential vulnerabilities that may affect them.
It is a methodology for security assessment that avoids the subjectivity typically involved in asset and risk evaluation.
Its purpose is to determine the state of security in an operational environment, taking into account controls (security measures), interactions, and limitations (weaknesses or vulnerabilities) that may arise.
By applying this methodology, a value is obtained that indicates the state of operational security at a given point in time.
This methodology complies with the LOPD (Organic Law on Data Protection) and the LSSICE (Law on Information Society Services).
Security implementation and management
The security implementation and management projects require a good methodology in order to succeed. To do so, it is necessary to analyze the specific client needs and then implement those politics more appropriately for their environment.
During the project realization, from esCERT-UPC we analyze and contemplate the possible inclusion of the following components:
- High availability and Load balancing solutions
- Firewalls and VPN
- Pattern based NIDS and HIDS systems
- Anomaly detection systems
- Monitoring systems
- LOG correlation systems
- Automatic audit systems
- SIEM Systems
Incident Response
The UPC incident response team (esCERT-UPC) help schools and departments that have detected a possible incident in their networks.
To do so, we provide the necessary contact info to report, identify and analyze the facts, suggesting solutions and strategies to solve the problem.
If you think that your school or department has been involved in a security incident or if you have detected some kind of security problem in your systems and need the help of esCERT-UPC team, send us all the information to: cert@escert.upc.edu.
Compliance
The quality of information systems is a fundamental factor to succeed in projects of the TIC environment.
From esCERT-UPC we offer a set of services oriented to the compliance of this information systems with the current law::
- GDPR audits and Audits in observance of the Organic Law 15/1999 on the Protection of Personal Data (LOPD)
- LSSI audits
Services to UPC community
esCERT helps and advises in security and incident response in IT networks. The main goals of our organization are:
- Inform about security vulnerabilities and threats.
- Disclose and offer to the community information that can be used to prevent and resolve security incidents.
- Realize investigations related with computer security.
- Educate the community, in general, about security issues.
esCERT offers the UPC a service of incident response based on preventive and reactive measures.
The Preventive Support service offered by esCERT to UPC has the aim to help system administrators of the UPC to improve the security of their systems. All preventive measures have the objective to inform administrators about potential or real vulnerabilities of their systems and the appropriate solutions for their prevention.
The preventive measures that we offer are:
- Consulting: esCERT offers a technical consulting service through the email cert@escert.upc.edu.
- Audits: The information systems audits can help to detect vulnerabilities, with the objective of repairing them as soon as possible to minimize the threats that the organization is exposed to. More information about audits.
- Training: An adequate training of the administrators can help to have a better knowledge about digital security, so any implantation/integration of the information systems can be done focusing specially on the weakest points. In the UPC intranet you will be able to access to the training program of the current year, where you will see the different courses that esCERT will hold through the year.
The Reactive Support service offered by esCERT to the UPC has the goal of giving support to the system administrators of the UPC on the communication, management and resolution of computer security incidents, and of providing informs and statistics, and acting as the Coordinator Center in emergency situations.
The reactive measures are the following:
- Recomendations: In case you have been victim of an attack, in esCERT we are willing to offer guides and recommendations suitable for your case to be able to manage the incident.
- Forensic Analysis: We offer the possibility of realizing forensic analysis on your systems to detect the origin of the problem or even the organism responsible for the incident. More information about forensic analysis.
